2019 in Review
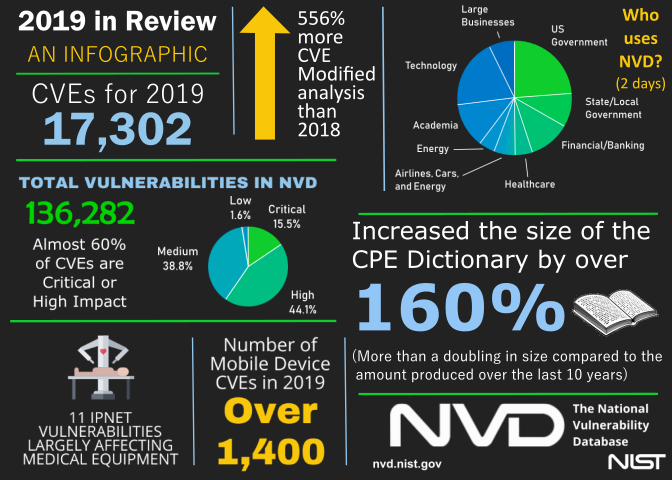
Over the past year, the NVD continued to see an increase in the number of vulnerabilities submitted for analysis. In 2019, 17,302 Common Vulnerabilities and Exposures, or CVEs, were submitted to the NVD. The analysts completed over 5,000 Modified CVEs and added 269,905 Common Platform Enumerations (CPEs) to the CPE Dictionary— an increase of 556% of Modified CVE analysis compared to 2018. Additionally, the CPE Dictionary grew by over 160% in one year, and the historical backlog of CVEs waiting to be processed was reduced to less than 15% of its previous size and is now manageable on a day-to-day basis.
Moving forward, the NVD Team has several strategies to gain efficiencies, provide better value, and meet future demands. Improvements in tools and workflow for the analysts are continuously being developed, and the team intends to implement
acceptance of CVE metadata from CVE Naming Authorities (CNAs). This would allow some CNAs to provide their own analyses of CVEs, and—after internal review—their assessments could automatically be accepted into the NVD. This process will be further described in NISTIR 8246,
National Vulnerability Database (NVD) Metadata Submission Guidelines for Common Vulnerabilities and Exposures (CVE) Numbering Authorities (CNAs) and Authorized Data Publishers, which is expected to be published in 2020. The team also plans to implement a vulnerability ontology, or vulntology—an approach that will be published for public comment in 2020—and determine whether natural language processing (i.e., artificial intelligence) will be useful in the future analyses of CVEs.


 ) or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure websites.
) or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure websites.
