Understanding Vulnerability Detail Pages
CVE Tags
CVE Tags are provided by a CNA and serve as a shorthand method to provide contextual data regarding the CVE Record. These tags are displayed at the top of the Vulnerability Detail page below the CVE ID.
| Tag | Description |
|---|---|
| Disputed | When one party disagrees with another party's assertion that a particular issue in software is a vulnerability, a CVE Record assigned to that issue may be tagged as being 'disputed'. |
| Unsupported When Assigned | Used by the assigning CNA to indicate that when a request for a CVE assignment was received, the product was already end-of-life (EOL) or a product or specific version was deemed not to be supported by the vendor. This tag should only be applied to a CVE Record when all affected products or version lines referenced in the CVE-Record are EOL. |
| Exclusively Hosted Service | All known software and/or hardware affected by this CVE Record is known to exist only in the affected hosted service. If the vulnerability affects both hosted and on-prem software and/or hardware, then the tag should not be used. |
The CVE Tags associated with a vulnerability are submitted through the CVE List and are maintained by the CNAs responsible for the CVE Record within the CVE Program. The NVD has no control over CVE Tags. If you feel that the information is inaccurate, please contact them using the form at https://cveform.mitre.org/.
Descriptions
These serve as a summary of the vulnerability and can include information such as the vulnerable product, impacts, attack vector, weakness or other relevant technical information. At times, CVEs may display a Current Description and Analysis Description, for example:
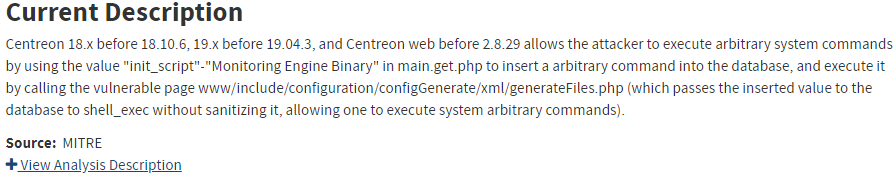
Current Descriptions are the descriptions that are available at the time of viewing, which may be different than the descriptions when enrichment was last performed. Analysis Descriptions are the descriptions that were available at the time of NVD enrichment. The image above displays a vulnerability with both. The Current Description is shown by default with the option to click ‘+’ to display the Analysis Description.
The descriptions associated with a vulnerability are submitted through the CVE List and are maintained by the CNA (CVE Numbering Authority) responsible for the CVE Record within the CVE Program. The NVD has no control over CVE descriptions. If you feel that the information is inaccurate, please contact them using the form at https://cveform.mitre.org/.
Metrics
The Common Vulnerability Scoring System (CVSS) is a method used to supply a qualitative measure of severity. CVSS is not a measure of risk. Each CVE in the dataset may have one or more CVSS vector strings of various versions (v2.0, v3.x, v4.0). CVSS vector strings consist of metrics. These metrics can be used in an equation or ranking methodology to determine a number ranging from 1-10. The higher the number, the higher the severity of the vulnerability. The CVSS specifications are available from the FIRST website and can be referenced at https://www.first.org/cvss/specification-document. As of July 13th, 2022, the NVD no longer generates new data for CVSS v2.0.
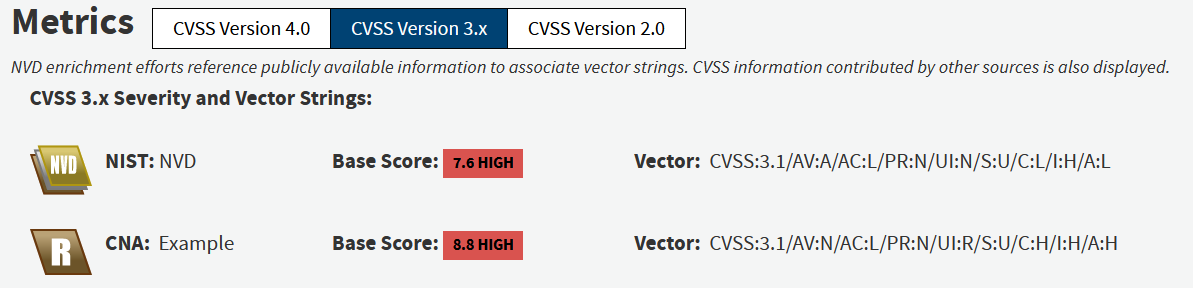
The NVD displays CVSS information based on the results of NVD enrichment. If the CNA responsible for the CVE record has provided CVSS information via the CVE List it will be displayed as well. In the event the CVSS information provided by both the NVD and the CNA matches, only the CNA provided CVSS information is displayed. Users can select which CVSS version they would like to view by using the button toggles.
References
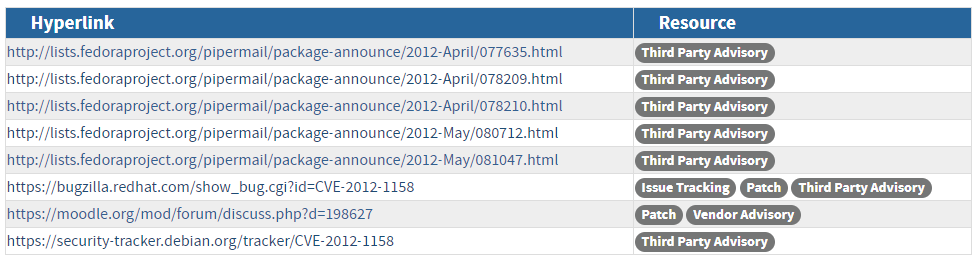
These URLs are supplemental information relevant to the vulnerability, which include details that may not be present in the CVE Description. References are given resource tags such as third-party advisory, vendor advisory, technical paper, press/media, VDB entries, etc. These tags can help users quickly categorize the type of information each reference contains. References for a CVE are provided through the CVE list, the NVD does not have direct control over them. If you have concerns with existing CVE references or find other publicly available information that would be useful, then you can submit a request using the form at https://cveform.mitre.org/ for the CVE Assignment Team to review.
Known Exploited Vulnerability
The Known Exploited Vulnerability section appears only when the CVE is included in CISA’s Known Exploited Vulnerabilities (KEV) Catalog. CISA strongly recommends all organizations review and monitor the KEV catalog and prioritize remediation of the listed vulnerabilities to reduce the likelihood of compromise by known threat actors.
Questions about the Known Exploited Vulnerabilities Catalog should be directed to CISA. Questions about the CVE data should be directed to the NVD.

Weakness Enumeration
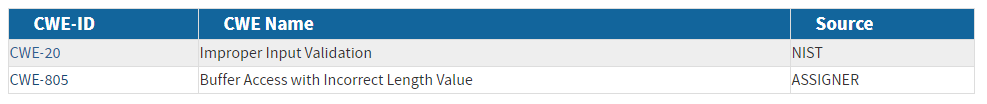
The NVD uses Common Weakness Enumeration (CWE), which was created to identify common software security weaknesses. The CWE list took community initiative of organizations and researchers to create specific definitions for each security flaw. The NVD uses the CWE-1003 view when associating CWEs to vulnerabilities. Known as “Weaknesses for Simplified Mapping of Published Vulnerabilities”, this subset of CWEs was selected through coordination between the NVD and the CWE team. If the CNA of the CVE record has provided CWE information via the CVE List it will be displayed in this section along with the CWE[s] associated through NVD enrichment.
Known Affected Software Configurations
This section of the vulnerability detail page is used to show what software or combinations of software are considered vulnerable at the time of enrichment. The NVD uses the Common Platform Enumeration (CPE) 2.3 specification when creating these applicability statements and the matching CPE Name(s). Applicability statements are a way to communicate which products are vulnerable in a relatively flexible syntax. This was designed primarily to be processed by machines and thus is not easy to digest for human readers. We have made attempts to represent this information in a more human readable way while still reflecting the products as they exist in the CPE Dictionary. Configurations are labeled numerically, however, there is no configuration considered to be of greater importance than the others. Each configuration communicates which products, platforms and/or hardware are thought to be vulnerable.
Configurations
A configuration is a container that holds a set of nodes which then contain CPE Name Match Criteria. Configurations consist of three different types.
| Basic | A single node containing one or more sets of match criteria. This configuration type communicates that each CPE Name that matches the match criteria is considered vulnerable. |

|
| Running On/With | A combination of nodes containing both vulnerable and non-vulnerable match criteria. This configuration type communicates that CPE Names that match the match criteria from both nodes must be present before a vulnerability applies. |
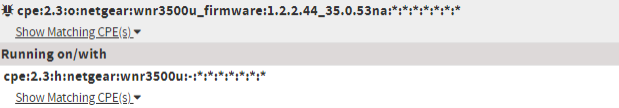
|
| Advanced | A complex combination of nodes with many enumerations based on the CPE 2.3 specification. Advanced configurations are displayed with the actual nodes and node values on the vulnerability detail page instead of in a simplified form such as the Basic and Running On/With configuration types. |
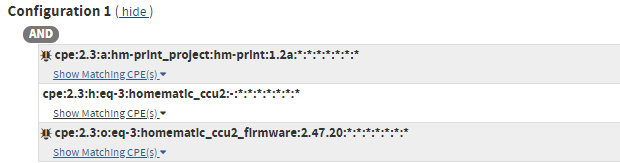
|
Match Criteria
Applicability statements are made to withstand changes to the Official CPE Dictionary without requiring consistent maintenance. CPE Match criteria comes in two forms CPE Match Strings and CPE Match String Ranges. Each of these are abstract concepts that are then correlated to CPE Names in the Official CPE Dictionary. Match criteria are displayed in bold text within a configuration node.
CPE Match Strings
A CPE Match string is a single CPE Names string that correlates to one or many CPE Names in the Official CPE Dictionary. When a match string has the bug icon next to it, all matching CPE Names are considered vulnerable. You can click the caret below a CPE Match String to see the CPE Names in the dictionary that match.

CPE Match String Range
A CPE Match String Range is very similar to the CPE Match String, but instead of having a single version assignment, it can have both a start and end version assignment. CPE Match String Ranges can represent <, >, <=, >= within a boundary. Instead of listing out a match string for all versions of a product between 17.011.30059 and 17.011.30099 a CPE Match string range will have a start version of 17.011.30059 and an end version of 17.011.30099. When a CPE Match String Range has the bug icon next to it, all matching CPE Names are considered vulnerable. You can click the caret below a CPE Match String Range to see the CPE Names in the dictionary that match.
- The base match string. This is combined with the Start/End version to identify matched CPE Names
- The Start version. “From (including) is the same as “>=”
- The End version. “Up to (including)” is the same as “<=”
- Vulnerable identifier

CPE Names
A Common Platform Enumeration Name is a unique string used to identify a specific enumeration of a product. Once a product is identified, a CPE Names must be submitted and approved to the Official CPE Dictionary for it to show up in the results of any applicable match criteria. CPE Names are displayed in italic text and are hyperlinks to the applicable CPE Detail page.
CPE Names can be deprecated for multiple reasons, this means that the unique string is no longer considered accurate and instead a different string should be used. When a deprecated CPE Names matches, it is displayed with strikethrough text and the resulting appropriate CPE Name is indented underneath.
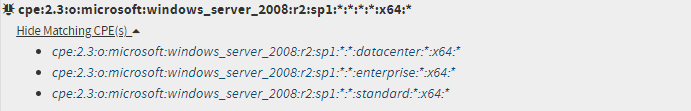

CPE Match String or Name Missing?
Let us know! Public Information on vulnerabilities changes daily, please contact the NVD team using the alias [email protected] and we will work to resolve any data issues as time and resources allow.

 ) or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure websites.
) or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure websites.
